IPv6, Secure and Private AI are both upon us, and Cohesive Networks is delivering into those areas with the same practical approach we have used for Public and Private Cloud all these years.
Stand Apart – but be Cohesive
I received a number of congratulations on the LinkedIn platform last month when apparently it let people know I have been with Cohesive Networks for 9 years.
As I reflected on this one thing stands out in relief, and that is Cohesive has always “stood apart” within the markets it serves.
Cohesive Networks exists at the confluence of virtualization, cloud, networking and security. We are of course a part of this commercial market but have not been re-directed by every twist and turn of these markets that have come and gone. Flavor and fashion are often the order of the day, and no doubt we have adopted some of the descriptive labels through time. But the labels have not swayed us from our essential mission, getting customers to, through and across the clouds safely.
If you look at the Gartner hype cycle for cloud networking it provides a gallery of differentiators through time: network observability, container/kubernetes networking, multicloud networking, SASE, SSE, Network-as-a-Service, SD-branch, network automation, network function virtualization, software defined networking, zero trust networks, software-defined WAN, micro-segmentation. If you look at these different facets, the tools, techniques, and knowledge to implement these are not that different. What is different is the packaging and the go-to-market.
Because we have been providing a virtual network platform since the clouds began, we have had customers use us for all of these functions. As a result the good news is we have been less “swayed” by flavor and fashion, which has done well for our existing customer. The bad news is we haven’t always best communicated our value to the potential new customer who may be thinking very much in the context of one of these re-packaged approaches.
Our usual inbound leads are “Hi, I think we need your stuff” or “Hi, we are using a lot of your stuff, can we discuss volume discounts and support plans”.
This communication posture stems from the fact that we have often been ahead of our competitors in either implementation or insight, or both. We were the first virtual network appliance in the EC2 cloud, IBM Cloud, many of the “clouds no-more”, and at later dates among the first network and security appliances in Azure and Google.

Cohesive’s patents are for “user controlled networking in 3rd party computing environments”. It is a subtle distinction – but powerful, between what an infrasturcture administrator, network administrator or hypervisor administrator could do at that time, and the freedom of our users on that infrastructure to create any network they wanted. These are encrypted, virtual networks that their infrastructure providers know nothing about, can not see, nor control. Our users in 2009 and beyond could create any secure, mesh, over-the-top network they wanted without the need or expense of the network incumbents who came before us. These customers find us significantly easier, significantly less expensive and made for the cloud without “metal” roots dragging them back to the ground.
When we showed this capability to investors, partners, infra providers, acquirerers – many of them said “I don’t get it” or “we’ll do better (someday)” or “you have to do all this in hardware” and more. By comparison, the customers who found us through web search, cloud conferences, and cloud marketplaces said “that’s what I need” and a subscription cloud networking company was born.

Looking back, it is shocking that our first offering was “virtual subnets”. It is amazing to think about it, but we sold subnets! At that time any cloud you used put your virtual instances in a very poorly segmented 10.0.0.0/8 subnet of the compute virtualization environment. People wanted to control addresses, routes, and rules, and our encrypted mesh overlay provided it. That was our first product-market fit, and of course that has evolved considerably.
This set us on the path of listening to our customers, and asking ourselves quite fundamentally what a network is, and what is it used for, and by whom?
So while we stood apart, of course we were Cohesive.
Networks are all about standards and interoperability, we just did it our own way.
The feedback from customers was “yes” and “more please”. The feedback from the experts often remained “huh”. So we pressed forward in our own autonomic and somewhat autistic manner, only listening to certain market signals and obsessively working to fulfill a vision of networking and security that says “networks are addresses, routes and rules, everything else is implementation detail the customers should rarely see.”

Now in 2024 and beyond, as the chaotic streams of the changing cloud markets, Internet Protocol v6, and the needs for secure AI and private AI collide, my guess is we will still stand apart while still being Cohesive.

Navigating the Cloud Transition: Simplified Solutions for Legacy Applications
source:Dall-E
Overcoming the Complexities of Cloud Migration with Cohesive Networks’ VNS3 Plugin System
Transitioning legacy applications to the cloud can be a daunting task. The challenges are numerous: complex network reconfigurations, increased costs, extended downtimes, and potential security risks. These hurdles are particularly pronounced for applications that rely on broadcast functionality, a common feature in many legacy systems yet challenging to implement in cloud environments – and entirely missing from the offerings of today’s major cloud providers.
Addressing the Core Challenges:
Complex Network Reconfiguration:
Legacy applications often depend on specific network features, like Layer 2 broadcast, which aren’t natively supported in cloud environments. Reconfiguring these applications for cloud networks usually means extensive and costly alterations.
Cost and Resource Allocation:
Moving to the cloud shouldn’t mean breaking the bank or pushing back deadlines. Traditional methods involve hiring specialists or investing in extensive development work, leading to spiraling costs and repeated delays.
Downtime and Operational Delays:
Every minute your application isn’t fully operational impacts your business. Lengthy transitions and testing periods are common with traditional cloud migration methods. The more your application has to change to fit a new environment, the greater the chances for costly mistakes.
Security Concerns:
Adapting legacy applications to the cloud can introduce vulnerabilities, especially when modifying network architectures. New code means new bugs, and new configuration introduces opportunities for human error.
The VNS3 Solution
At Cohesive Networks, we’ve developed a new plugin for our VNS3 software that specifically addresses these issues for applications requiring broadcast functionality. Our solution allows for a seamless and efficient transition to the cloud, without the need for extensive network reconfiguration or application rewriting.
Ease of Use:
With our plugin, most broadcast-dependent applications can be migrated to the cloud with minimal setup and no changes to the existing code or application workflow.
Cost-Effective:
Our approach significantly reduces the need for expensive network specialists, extensive redevelopment, offering a more budget-friendly solution.
Minimized Downtime:
Our streamlined process ensures a faster and smoother transition, reducing operational disruptions. HA and failover options mean that you won’t sacrifice the inherent reliability of cloud environments.
Secure Transition:
VNS3 maintains a strong security posture throughout the migration process, ensuring your data and applications are protected.
Your Path to Cloud Efficiency
Embrace the future of cloud networking with Cohesive Networks. VNS3 isn’t just a tool; it’s a comprehensive solution that makes your cloud networking efficient, secure, and cost-effective. Experience a smoother transition and enable your applications to thrive in a new cloud environment with ease and confidence.
Contact a Cohesive Networks expert today for real solutions that provide real value.

Apple VisionPro – No security issues yet!
This front image of the Apple VisionPro augmented reality headset is apt at the moment.
It is dark and we can’t see clearly yet, which is OK, because it allows us the opportunity to prognosticate.
In addition, no network or security issues yet!
We still have time to panic.
Although devices are not a normal topic for us at Cohesive Networks, as CTO, I thought I would ruminate a bit at LinkedIn in a post on The Apple Impact (2023).
Whilst the future is a bit murky, the AI breakout and VisionPro for AR (augmented reality) will combine in interesting ways: compelling, practical, frightening, and unanticipated.
From a Cohesive point of view, as we provide over-the-top networks and security to, through and across the clouds, both of these trends are going to have an impact with Large Language Models deep in the clouds, and augmented reality as the lens from below, piercing the cloud cover.
From a personal point of view:
“Vision Pro emerges at the same time as the artificial intelligence breakout. What will these gods of unknown intention be whispering in our ears? I can’t quite yet imagine these two emergent technologies combined and how it could bring about completely new social environments – with all the good and all the terrible amplified.”
We would love to hear what you think.
Native WireGuard® Clients and VNS3 6.0 Beta2
VNS3 6.0 Beta2 is now available.
You can find the Free edition in both the Amazon and Azure marketplaces (GCP coming soon).
It is an easy way to get a server up and running that can connect you to data centers, cloud VPCs/VNETs, has a super firewall, straightforward support of even difficult things like “source based routing”, and most of all a quick way to run and manage your own WireGuard® network connecting multiple people, devices, or both.
This post will show you how to use the standard Mac Appstore WireGuard client built and delivered by the WireGuard team with Cohesive Networks VNS3 6.0 network controllers. (Of course similar capability is available using the same app from the Windows/iPhone/Android “app stores” as well.)
In future posts we will show the Cohesive CLI (cnvpn) at work, and the Cohesive WG GUI working with VNS3 6.0. And then we will follow up by showing how the different connection options work with a distributed VPN cluster where you can spread a VNS3 controller mesh across regions and clouds with ease, yet have a unified VPN system for management of credentials, pre-shared keys, OIDC sessions and more.
In the screen shots throughout we have three windows; upper left the Mac OS WG client, bottom left a command line from the same Mac, and to the right the cloud-based VNS3 server supporting a wide range of cloud networking use-cases, and here specifically WireGuard VPN connections.
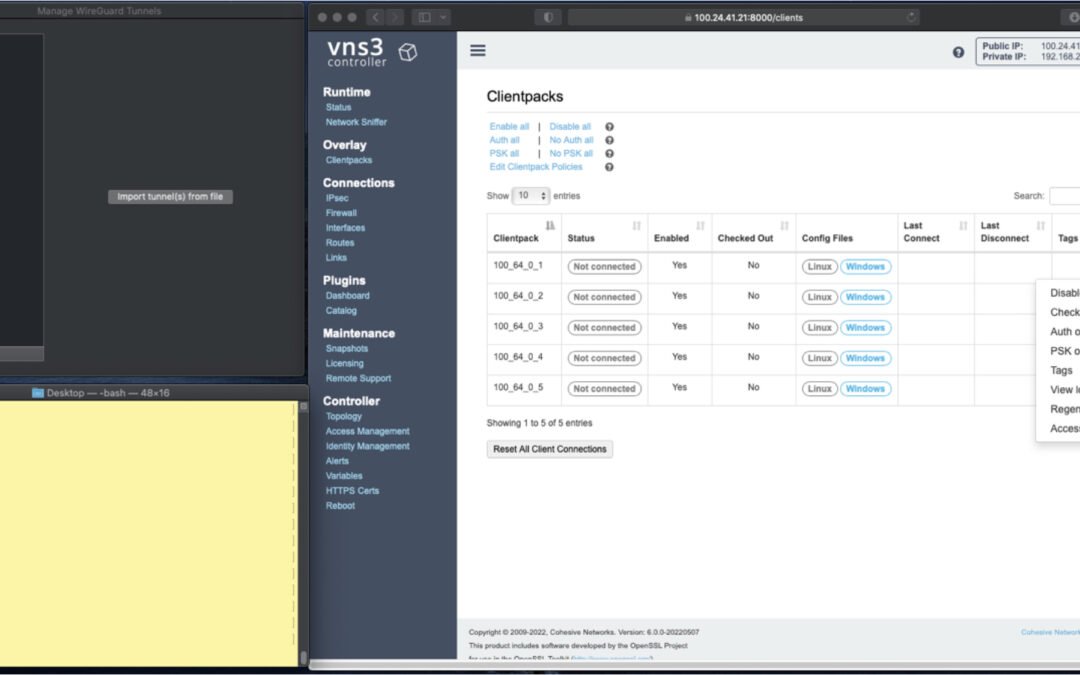
VNS3 Network Platform has the concept of “clientpacks” – basically the credentials needed to connect a machine or a person via a VPN client to the network. Historically they have been “openvpn” by default – and starting in 6.0 they are WireGuard by default. In a future release we will support a dual stack with both “ovpn” and “wg” connections simultaneously, and a goal of IPsec clients as well.
In the picture above and those below we see the “Clientpacks” page. From here you can perform key administrative functions like disabling addresses, re-generating credentials, updating pre-shared keys, and getting access URLs for secure and easy distribution of VPN credentials.

Above shows the results of choosing “Access URL” and displaying its result. This is a secure, one-time, timed URL which allows users to copy/paste the clientpack, download it for import, or for mobile clients use a QR code for import.
It has all the necessary information to make a connection using the standard WG Client – with or without PSKs.
There is also a series of commented lines which are used by CNVPN CLI and GUI for additional enterprise support (failover, dynamic route updates, OIDC authentication) to be discussed in future. For now we just want to focus on how easy it is to connect native WG clients.
Copy/paste the clientpack into the Mac OS client, and click SAVE/ACTIVATE.

Voilà – you are connected to the VPN. The VNS3 Clientpacks page shows the status as “connected”.
The WG Client now shows its statistics about the connection, and below we are pinging the VNS3 controller’s VPN address to show access to the VPN network.
(By default, this connection can access other addresses on the VPN. If that’s not desired it is easily changed via the Firewall page.)

If needed you can use the Action menu to perform administrative operations. For example, if you select “Disable” on the connection, the client is dropped from the VPN. Below, we see the client set to disabled state by the Admin, and we see the “pings” begin to fail.
Then we “Enable” – and the client is back on the network and packets begin to flow.


And of course similar operations can be performed to re-new or re-secure a connection by adding a PSK or re-generating keys – both of which require the clientpack to be redistributed to the user or device. But as expected, when you enable a PSK for the connection, the user is unable to access the network. With the credential re-deployed with the appropriate clientpack containing the PSK, they are back on the net!


Accessing the other devices on the VPN network is one use, what about getting to the Internet?
This requires a couple configuration elements on the client side which requires a little bit of operating system knowledge on the client side and a of couple firewall rules on the VNS3 Controller. We won’t go into those specifics here.
But, if you look at the Cohesive-specific directives used by the CNVPN CLI and GUI – one of them is “TunnelAllTraffic” – and when this is set to “true” – all the client side magic is done for you! But that is for another day.
(“WireGuard” and the “WireGuard” logo are registered trademarks of Jason A. Donenfeld.)

Announcing Successful Type 2 Soc 2 Examination
We’re happy to announce that Cohesive Networks has successfully completed a Type 2 SOC 2 examination. The examination confirmed that our systems are protected against unauthorized access, unauthorized disclosure of information, and damage to systems that could compromise the availability, integrity, confidentiality, and privacy of information or systems.
Examination Details
- Selected SOC 2 Categories: Security
- Examination Type: Type 2
- Review Period: November 1, 2021, to April 30, 2022
- Service Auditor: Schellman & Company, LLC
Our Secure History
Security and privacy are at the core of our business model and part of our culture. Cohesive Networks was spun out in 2014 from Cohesive Flexible Technologies in part due to a realization we were no longer in the cloud migration business. We were in fact a security and networking company. As a result we had the opportunity and experience to create internal systems and controls to a high standard. All are still overbuilt by today’s measure.
By design, we have no access to customers’ VNS3 provided networks. Access and visibility are completely in the hands of the owner. Given that deployment mode, VNS3 has mechanisms to ensure limited attack surface with no backdoor access: Access URLs and API Tokens.
We also “eat our own cooking.” VNS3 was created by our parent company, Cohesive Flexible Technologies back in 2008. The purpose was first to secure our Elastic Server product cluster (see Bill-of-Materials approach to virtual machine image creation) and second to provide IP address control and security for the wild west EC2-classic 10/8 network space of the day. Our company runs internal Overlay Networks for our production systems, support engineers, as well as PeopleVPN for our remote/post-geographic team.
Future Plans
Cohesive Networks is committed to continuing annual Type 2 SOC 2 examinations and will plan on adding Availability and Privacy Trust Service categories in the future. Additionally we’ll be evaluating if a SOC 3 examination is more appropriate given our role as a provider of critical network infrastructure for our globally distributed customer base.

News Roundup: Week of Feb 21, 2022
U.S. Cyber Officials Issue Official Warning Against Potential Russian Cyber Attacks
During a call this Monday, FBI and DHS cyber officials urged government agencies “to look out for signs of Russian activity on their networks” as a result of the evolving Ukraine crisis. According to Yahoo: “federal officials also urged those on the call to dramatically lower their threshold for reporting suspicious activity.” Citing “an uptick in Russian scanning of U.S. law enforcement networks” as well as “in Russian disinformation and misinformation about Ukraine,” cyber officials urge increased care and caution with links and communications as the crisis progresses.
IBM Opens Cyber Security Hub in India
IBM recently announced the opening of their first IBM Security Command Center in the Asia Pacific region. The center hopes to provide a cybersecurity incident response plan for enterprise customers with deployments in the region, as well as “a fully immersive, interactive, and experiential learning facility.” IBM plans to use simulations and experiential training to help enterprises protect themselves from cyberattacks. IBM promises that by co-locating this training center with their X-Force Command Center, IBM’s Security Operations Center, both live practice and training for cyber security precautions will benefit immensely.
Microsoft Brings Cloud Security to GCP
Yesterday Microsoft announced the release of Microsoft Defender for Cloud for Google Cloud Platform, making Microsoft the first major cloud provider to offer security solutions in all major cloud platforms. The offering from Microsoft boasts Cloud Security Posture Management (CSPM) and Cloud Workload Protection (CWP) across both containers and servers. According to the release, GCP deployments of Microsoft Defender for Cloud will come “with out-of-box recommendations that allow you to configure GCP environments in line with key security standards like the Center for Internet Security (CIS).” Microsoft is also emphasizing the necessity of Zero Trust Management and event log management in cloud environments with two more ‘upgraded’ cloud security offerings.





Recent Comments